All tutorilas about hacking wifi. From basic to advanced. It took only 2 hours, We can use wifi free everywhere, everywhen.
Hacking Videos-Part1 / videos_pt1 / 128 Bit Wep Cracking With Injection!.swf 13 MB
Hacking Videos-Part1 / videos_pt1 / Adding Modules to a Slax or Backtrack Live CD from Windows.swf 4.2 MB
Hacking Videos-Part1 / videos_pt1 / Basic Nmap Usage!.swf 8.3 MB
Hacking Videos-Part1 / videos_pt1 / BufferOverflowPart2-Shellcoding ByIDEspinner.avi 12.7 MB
Hacking Videos-Part1 / videos_pt1 / BufferOverflowPart3ExploitsByIDEspinner.avi 15.2 MB
Hacking Videos-Part1 / videos_pt1 / How to decrypt SSL encrypted traffic using a man in the middle attack (Auditor).swf 32.2 MB
Hacking Videos-Part1 / videos_pt1 / Sniffing Remote Router Traffic via GRE Tunnels (Hi-Res).avi 121.5 MB
Hacking Videos-Part2 / A Quick and Dirty Intro to Nessus using the Auditor Boot CD!.swf 2.8 MB
Hacking Videos-Part2 / Breaking WEP in 10 minutes.avi 27.6 MB
Hacking Videos-Part2 / Complete Hacking Video using Metasploit – Meterpreter.swf 12.5 MB
Hacking Videos-Part2 / Cracking a 128 bit WEP key (Auditor).swf 50.6 MB
Hacking Videos-Part2 / Cracking a 128 Bit Wep key entering the cridentials.swf 22.1 MB
Hacking Videos-Part2 / Cracking Syskey and the SAM on Windows Using Samdump2 and John!.swf 2.5 MB
Hacking Videos-Part2 / Cracking Windows Passwords with BackTrack and the Online Rainbow Tables at Plain-Text!.swf 4.3 MB
Hacking Videos-Part2 / Cracking WPA Networks (Auditor).swf 14.8 MB
Hacking Videos-Part2 / DoS attack against Windows FTP Server – DoS.avi 10 MB
Hacking Videos-Part2 / Droop s Box Simple Pen-test Using Nmap, Nikto, Bugtraq, Nslookup and Other Tools!.swf 6.6 MB
Hacking Videos-Part2 / Exploiting some bugs of tools used in Windows.swf.swf 16 MB
Hacking Videos-Part2 / Exploiting weaknesses of PPTP VPN (Auditor).swf 5.5 MB
Hacking Videos-Part2 / Finding Rogue SMB File Shares On Your Network!.swf 5.5 MB
Hacking Videos-Part2 / Fun with Ettercap Filters!.swf 2.4 MB
Hacking Videos-Part2 / How to crack the local windows passwords in the SAM database .swf 6.8 MB
Hacking Videos-Part2 / How to sniff around switches using Arpspoof and Ngrep!.avi 3.2 MB
Hacking Videos-Part3 / Anonym.OS LiveCD with build in Tor Onion routing and Privoxy.swf 3.3 MB
Hacking Videos-Part3 / BackTrack LiveCD to HD Installation Instruction Video .swf 7.1 MB
Hacking Videos-Part3 / Basic Tools for Wardriving!.swf 2.7 MB
Hacking Videos-Part3 / Bluesnarfer attack tool demonstration.swf 9.8 MB
Hacking Videos-Part3 / IDEspinner Buffer Overflows pt1.avi 2.5 MB
Hacking Videos-Part3 / IDEspinner Feature Addition pt2.avi 11.3 MB
Hacking Videos-Part3 / IDEspinnerDNS-PoisonRouting.avi 5 MB
Hacking Videos-Part3 / Install VNC Remotely!.avi 2.9 MB
Hacking Videos-Part3 / Internet Explorer Remote Command Execution Exploit (CMDExe) Client Side Attack (Hi-Res).avi 25.7 MB
Hacking Videos-Part3 / Internet Explorer Remote Command Execution Exploit (CMDExe) Client Side Attack (Lo-Res).avi 19.9 MB
Hacking Videos-Part3 / John The Ripper 1.7 password cracker Installation Instruction Video .swf 2.6 MB
Hacking Videos-Part3 / Local Password Cracking Presentation for the Indiana Higher Education Cybersecurity Summit 2005!.swf 5.7 MB
Hacking Videos-Part3 / MAC Bridging with Windows XP and Sniffing!.swf 1.4 MB
Hacking Videos-Part3 / Mass De-Authentication using void11 (Auditor).swf 16.5 MB
Hacking Videos-Part3 / Metasploit Flash Tutorial!.swf 3.2 MB
Hacking Videos-Part3 / MITM Hijacking.wmv 52.3 MB
Hacking Videos-Part3 / Nmap Video Tutorial 2 Port Scan Boogaloo!.swf 13.4 MB
Hacking Videos-Part3 / Sniffing logins and passwords.avi 7.1 MB
Hacking Videos-Part4 / A Penetration Attack Reconstructed.avi 40.2 MB
Hacking Videos-Part4 / Bluesnarfing a Nokia 6310i hand set.avi 11.5 MB
Hacking Videos-Part4 / Cain to ARP poison and sniff passwords!.avi 1.7 MB
Hacking Videos-Part4 / Sniffing Remote Router Traffic via GRE Tunnels (Lo-Res).avi 71 MB
Hacking Videos-Part4 / Sniffing VoIP Using Cain!.swf 1.7 MB
Hacking Videos-Part4 / Snort Instruction video – howto install into backtrack.swf 10.6 MB
Hacking Videos-Part4 / SSH Dynamic Port Forwarding!.swf 3 MB
Hacking Videos-Part4 / Start a session and get interactive commandline access to a remote Windows box!.avi 5 MB
Hacking Videos-Part4 / Telnet Bruteforce.avi 18.9 MB
Hacking Videos-Part4 / Tunneling Exploits through SSH.avi 18.1 MB
Hacking Videos-Part4 / Use Brutus to crack a box running telnet!.avi 1.7 MB
Hacking Videos-Part4 / Using NetworkActiv to sniff webpages on a Wi-Fi network!.swf 1.3 MB
Hacking Videos-Part4 / WEP Cracking using Aireplay v2.2 Beta 7 (Whax 3.0).swf 5.2 MB
Hacking Videos-Part4 / WMF File Code Execution Vulnerability With Metasploit!.swf 3.7 MB
Hacking Videos-Part4 / WPA Cracking using Aireplay v2.2 Beta 7 (Whax 3.0).swf 5.2 MB
Hacking Videos-Part5 / BackTrack LiveCD to HD Installation Instruction Video .swf 7.1 MB
Hacking Videos-Part5 / Basic Nmap Usage!.swf 8.3 MB
Hacking Videos-Part5 / Basic Tools for Wardriving!.swf 2.7 MB
Hacking Videos-Part5 / Bluesnarfer attack tool demonstration.swf 9.8 MB
Hacking Videos-Part5 / Bluesnarfing a Nokia 6310i hand set.avi 11.5 MB
Hacking Videos-Part5 / Breaking WEP in 10 minutes.avi 27.6 MB
Hacking Videos-Part5 / Complete Hacking Video using Metasploit – Meterpreter.swf 12.5 MB
Hacking Videos-Part5 / Cracking Syskey and the SAM on Windows Using Samdump2 and John!.swf 2.5 MB
Hacking Videos-Part5 / Cracking Windows Passwords with BackTrack and the Online Rainbow Tables at Plain-Text!.swf 4.3 MB
Hacking Videos-Part5 / Cracking WPA Networks (Auditor).swf 14.8 MB
Hacking Videos-Part5 / DoS attack against Windows FTP Server – DoS.avi 10 MB
Hacking Videos-Part5 / Exploiting some bugs of tools used in Windows.swf.swf 16 MB
Hacking Videos-Part5 / How to crack the local windows passwords in the SAM database .swf 6.8 MB
Hacking Videos-Part5 / How to decrypt SSL encrypted traffic using a man in the middle attack (Auditor).swf 32.2 MB
Hacking Videos-Part5 / Install VNC Remotely!.avi 2.9 MB
Hacking Videos-Part5 / John The Ripper 1.7 password cracker Installation Instruction Video .swf 2.6 MB
Hacking Videos-Part5 / Local Password Cracking Presentation for the Indiana Higher Education Cybersecurity Summit 2005!.swf 5.7 MB
Hacking Videos-Part5 / MAC Bridging with Windows XP and Sniffing!.swf 1.4 MB
Hacking Videos-Part5 / Metasploit Flash Tutorial!.swf 3.2 MB
Hacking Videos-Part5 / SSH Dynamic Port Forwarding!.swf 3 MB
Hacking Videos-Part5 / Start a session and get interactive commandline access to a remote Windows box!.avi 5 MB
Hacking Videos-Part1 / videos_pt1 / Adding Modules to a Slax or Backtrack Live CD from Windows.swf 4.2 MB
Hacking Videos-Part1 / videos_pt1 / Basic Nmap Usage!.swf 8.3 MB
Hacking Videos-Part1 / videos_pt1 / BufferOverflowPart2-Shellcoding ByIDEspinner.avi 12.7 MB
Hacking Videos-Part1 / videos_pt1 / BufferOverflowPart3ExploitsByIDEspinner.avi 15.2 MB
Hacking Videos-Part1 / videos_pt1 / How to decrypt SSL encrypted traffic using a man in the middle attack (Auditor).swf 32.2 MB
Hacking Videos-Part1 / videos_pt1 / Sniffing Remote Router Traffic via GRE Tunnels (Hi-Res).avi 121.5 MB
Hacking Videos-Part2 / A Quick and Dirty Intro to Nessus using the Auditor Boot CD!.swf 2.8 MB
Hacking Videos-Part2 / Breaking WEP in 10 minutes.avi 27.6 MB
Hacking Videos-Part2 / Complete Hacking Video using Metasploit – Meterpreter.swf 12.5 MB
Hacking Videos-Part2 / Cracking a 128 bit WEP key (Auditor).swf 50.6 MB
Hacking Videos-Part2 / Cracking a 128 Bit Wep key entering the cridentials.swf 22.1 MB
Hacking Videos-Part2 / Cracking Syskey and the SAM on Windows Using Samdump2 and John!.swf 2.5 MB
Hacking Videos-Part2 / Cracking Windows Passwords with BackTrack and the Online Rainbow Tables at Plain-Text!.swf 4.3 MB
Hacking Videos-Part2 / Cracking WPA Networks (Auditor).swf 14.8 MB
Hacking Videos-Part2 / DoS attack against Windows FTP Server – DoS.avi 10 MB
Hacking Videos-Part2 / Droop s Box Simple Pen-test Using Nmap, Nikto, Bugtraq, Nslookup and Other Tools!.swf 6.6 MB
Hacking Videos-Part2 / Exploiting some bugs of tools used in Windows.swf.swf 16 MB
Hacking Videos-Part2 / Exploiting weaknesses of PPTP VPN (Auditor).swf 5.5 MB
Hacking Videos-Part2 / Finding Rogue SMB File Shares On Your Network!.swf 5.5 MB
Hacking Videos-Part2 / Fun with Ettercap Filters!.swf 2.4 MB
Hacking Videos-Part2 / How to crack the local windows passwords in the SAM database .swf 6.8 MB
Hacking Videos-Part2 / How to sniff around switches using Arpspoof and Ngrep!.avi 3.2 MB
Hacking Videos-Part3 / Anonym.OS LiveCD with build in Tor Onion routing and Privoxy.swf 3.3 MB
Hacking Videos-Part3 / BackTrack LiveCD to HD Installation Instruction Video .swf 7.1 MB
Hacking Videos-Part3 / Basic Tools for Wardriving!.swf 2.7 MB
Hacking Videos-Part3 / Bluesnarfer attack tool demonstration.swf 9.8 MB
Hacking Videos-Part3 / IDEspinner Buffer Overflows pt1.avi 2.5 MB
Hacking Videos-Part3 / IDEspinner Feature Addition pt2.avi 11.3 MB
Hacking Videos-Part3 / IDEspinnerDNS-PoisonRouting.avi 5 MB
Hacking Videos-Part3 / Install VNC Remotely!.avi 2.9 MB
Hacking Videos-Part3 / Internet Explorer Remote Command Execution Exploit (CMDExe) Client Side Attack (Hi-Res).avi 25.7 MB
Hacking Videos-Part3 / Internet Explorer Remote Command Execution Exploit (CMDExe) Client Side Attack (Lo-Res).avi 19.9 MB
Hacking Videos-Part3 / John The Ripper 1.7 password cracker Installation Instruction Video .swf 2.6 MB
Hacking Videos-Part3 / Local Password Cracking Presentation for the Indiana Higher Education Cybersecurity Summit 2005!.swf 5.7 MB
Hacking Videos-Part3 / MAC Bridging with Windows XP and Sniffing!.swf 1.4 MB
Hacking Videos-Part3 / Mass De-Authentication using void11 (Auditor).swf 16.5 MB
Hacking Videos-Part3 / Metasploit Flash Tutorial!.swf 3.2 MB
Hacking Videos-Part3 / MITM Hijacking.wmv 52.3 MB
Hacking Videos-Part3 / Nmap Video Tutorial 2 Port Scan Boogaloo!.swf 13.4 MB
Hacking Videos-Part3 / Sniffing logins and passwords.avi 7.1 MB
Hacking Videos-Part4 / A Penetration Attack Reconstructed.avi 40.2 MB
Hacking Videos-Part4 / Bluesnarfing a Nokia 6310i hand set.avi 11.5 MB
Hacking Videos-Part4 / Cain to ARP poison and sniff passwords!.avi 1.7 MB
Hacking Videos-Part4 / Sniffing Remote Router Traffic via GRE Tunnels (Lo-Res).avi 71 MB
Hacking Videos-Part4 / Sniffing VoIP Using Cain!.swf 1.7 MB
Hacking Videos-Part4 / Snort Instruction video – howto install into backtrack.swf 10.6 MB
Hacking Videos-Part4 / SSH Dynamic Port Forwarding!.swf 3 MB
Hacking Videos-Part4 / Start a session and get interactive commandline access to a remote Windows box!.avi 5 MB
Hacking Videos-Part4 / Telnet Bruteforce.avi 18.9 MB
Hacking Videos-Part4 / Tunneling Exploits through SSH.avi 18.1 MB
Hacking Videos-Part4 / Use Brutus to crack a box running telnet!.avi 1.7 MB
Hacking Videos-Part4 / Using NetworkActiv to sniff webpages on a Wi-Fi network!.swf 1.3 MB
Hacking Videos-Part4 / WEP Cracking using Aireplay v2.2 Beta 7 (Whax 3.0).swf 5.2 MB
Hacking Videos-Part4 / WMF File Code Execution Vulnerability With Metasploit!.swf 3.7 MB
Hacking Videos-Part4 / WPA Cracking using Aireplay v2.2 Beta 7 (Whax 3.0).swf 5.2 MB
Hacking Videos-Part5 / BackTrack LiveCD to HD Installation Instruction Video .swf 7.1 MB
Hacking Videos-Part5 / Basic Nmap Usage!.swf 8.3 MB
Hacking Videos-Part5 / Basic Tools for Wardriving!.swf 2.7 MB
Hacking Videos-Part5 / Bluesnarfer attack tool demonstration.swf 9.8 MB
Hacking Videos-Part5 / Bluesnarfing a Nokia 6310i hand set.avi 11.5 MB
Hacking Videos-Part5 / Breaking WEP in 10 minutes.avi 27.6 MB
Hacking Videos-Part5 / Complete Hacking Video using Metasploit – Meterpreter.swf 12.5 MB
Hacking Videos-Part5 / Cracking Syskey and the SAM on Windows Using Samdump2 and John!.swf 2.5 MB
Hacking Videos-Part5 / Cracking Windows Passwords with BackTrack and the Online Rainbow Tables at Plain-Text!.swf 4.3 MB
Hacking Videos-Part5 / Cracking WPA Networks (Auditor).swf 14.8 MB
Hacking Videos-Part5 / DoS attack against Windows FTP Server – DoS.avi 10 MB
Hacking Videos-Part5 / Exploiting some bugs of tools used in Windows.swf.swf 16 MB
Hacking Videos-Part5 / How to crack the local windows passwords in the SAM database .swf 6.8 MB
Hacking Videos-Part5 / How to decrypt SSL encrypted traffic using a man in the middle attack (Auditor).swf 32.2 MB
Hacking Videos-Part5 / Install VNC Remotely!.avi 2.9 MB
Hacking Videos-Part5 / John The Ripper 1.7 password cracker Installation Instruction Video .swf 2.6 MB
Hacking Videos-Part5 / Local Password Cracking Presentation for the Indiana Higher Education Cybersecurity Summit 2005!.swf 5.7 MB
Hacking Videos-Part5 / MAC Bridging with Windows XP and Sniffing!.swf 1.4 MB
Hacking Videos-Part5 / Metasploit Flash Tutorial!.swf 3.2 MB
Hacking Videos-Part5 / SSH Dynamic Port Forwarding!.swf 3 MB
Hacking Videos-Part5 / Start a session and get interactive commandline access to a remote Windows box!.avi 5 MB
Download Links:





 Posted in:
Posted in: 









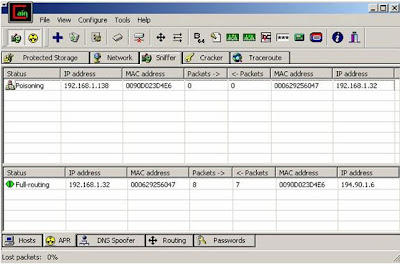






In my previous post I explained the basics of NIC,MAC and ARP. The main motive of that post was to build the grounds for ARP poisoning which I will explain in this post . In this post I will explain the concept behind it and then in my next tutorial on Cain and Able I will explain how it can be used for this hack.
In case you are not aware of technicalities of these terms then please refer the above link first .
This is a technique to attack LANs that use arp as the address resolution technique. This attack involves sending fake or spoofed messages onto a LAN and fool other machines .
Sniffing is the term used to describe the reading of all packets on a network segment. This is relatively easy on a network connected via a hub as ethernet is a broadcast medium and the attacker would only have to place his NIC in promiscuous mode to 'sniff' all traffic on that network segment. In a switched network this is not possible. This is because a switch builds a table of MAC addresses and their associated ports when the switch is powered on. When a host transmits an ethernet frame the switch examines the destination MAC address and routes the frame to the associated port as given in the switch table. Therefore it is not possible to sniff any traffic on the network.
There are two methods to sniff traffic in a switched environment using ARP Poisoning. The first is for the attacker to send multiple spoofed ARP Replies to the switch. The switch will process these replies, updating its table. If this is done at a rapid rate the switches table will overflow and the switch will default to broadcasting all traffic to all ports. The attacker can now 'sniff' all network traffic.
Host IP Address MAC Address
Host A 192.168.0.2 00:00:00:00:00:02
Host B 192.168.0.3 00:00:00:00:00:03
Attacker 192.168.0.4 00:00:00:00:00:04
Host IP Address MAC Address
Host A 192.168.0.2 00:00:00:00:00:02
Host B 192.168.0.3 00:00:00:00:00:04
Attacker 192.168.0.4 00:00:00:00:00:04
Host A 192.168.0.2 00:00:00:00:00:04
Host B 192.168.0.3 00:00:00:00:00:03
Attacker 192.168.0.4 00:00:00:00:00:04
The thing to keep in mind here is that the attacker must perform the two way poisoning so that it can recieve the packets as well as send it to the destination . In this way the connection will always be alive between the two communicating hosts and the attack will perform successfully.
To protect a hosts ARP cache from being poisoned it is possible to make it static. If an ARP cache has been made static it will not process any ARP Replies received unlike a dynamic ARP cache. This is not practical for large networks as the correct IP address to MAC address association of every host would have to be present in the cache of every host before it is made static. If one host changed its MAC address (e.g. after replacing a NIC) all hosts ARP caches would need to be updated manually. On windows a login script could automate this process however it has been reported Windows will still accept and process ARP Replies even when the ARP cache has been made static.
It is also possible to use Intrusion Detection Systems (IDS) to detect ARP Poisoning attacks. Arpwatch is a tool that will monitor a network for any changes in MAC address to IP address association, e-mailing the administrator should any such offence occur.
Stay tuned for my next post on how to perform ARP poisoning using Cain and Able.