This is my final post on the topic of ARP spoofing and poisoning . I hope you all have loved my other two posts in which I had built the grounds for understanding the basics of network protocols and ARP poisoning .
In case you want to read those post then here are the links :
Moving forward to the third and final post in this series , I will now focus on how we can use Cain and Able to perform the attack of ARP spoofing using this tool.
I will explain the other cool uses of this tool as well and then focus on how to use it as a sniffer.
Since I do not have a LAN setup to explain you with my own example so I picked up some good tutorials and papers from the net to explain you the things clearly .
I will explain the other cool uses of this tool as well and then focus on how to use it as a sniffer.
Since I do not have a LAN setup to explain you with my own example so I picked up some good tutorials and papers from the net to explain you the things clearly .
Here is the Download link for Cain and Able - Download
DESCRIPTION
Cain & Abel is a password recovery tool for Microsoft Operating Systems. It allows easy recovery of various kinds of passwords by sniffing the network, cracking encrypted passwords using Dictionary & Brute-Force attacks, decoding scrambled passwords, revealing password boxes, uncovering cached passwords and analyzingrouting protocols. It also has ARP poisoning and spoofing capabilities, making it into anextremely powerful hacking or auditing tool. The ARP spoofing feature works in a similar way as described in the "ARP Spoofing" tutorial. Indeed it would be wise to read that tutorial before attempting to use Cain.
Environment
1. Install and run Cain. Immediately when it opens you can see the first disturbing scene. All the cached passwords are shown in the "Protected Storage" tab. These include passwords from IE, Outlook or other HTTP transactions.
2. The "Network" tab is a scaled enumeration system, able of enumerating all Windows computers it can find on the local network.
3.The most interesting (IMHO) feature of Cain is in the "Sniffer" Tab. Cain allows you to ARPSpoof, Sniff and Brute force passwords all via one interface. Notice that the "Sniffer Tab" has 5 sub-tabs - Hosts, APR, DNS Spoofer, Routing and Passwords.
4. To start ARP Spoofing, you need to activate the sniffing daemon and the APR daemon. You do this by clicking on both the "Sniff" and "APR" buttons at the top of the window
5. Make sure you are in the "Sniffer" tab, and right click anywhere inside the tab. You should see a "Scan MAC addresses" option. Click it.
6. Choose the appropriate IP range that suits your local network and click "Ok".
7. A quick scan should occur, giving you all the MAC addresses present in that subnet.
8. Once the scan is complete, move to the APR sub-tab at the bottom of the window.This is the window in which you choose the computers you want to attack. Now click on the blue "plus" sign at the top of the windows to add hosts to attack.
9. You should get the following screen:
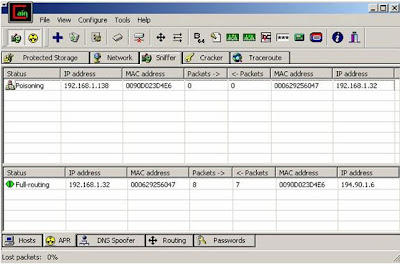
10. Now we wait for the attacked host to enter password data to services such as FTP, HTTP, POP3, IMAP, and lots of others. In the following screenshot, an FTP password was intercepted.
11. We can see that the FTP session between 192.168.1.32 (Attacked Computer) and 194.90.1.6 (Netvision's FTP server) was router via our computer. Now click on the "Passwords"see the captured passwords.
12. For encrypted passwords such as SMB (NTLM in it's various flavours) you can send the password to a Brute Force session.
13. After sending the password to the cracker, click on the "Cracker" tab and start the required attack.
This was a quick tutorial about Cain's ARP Spoofing ability. Apart from ARP Spoofing Cain can do lots of other wonderful things, just take time to *carefully* learn the application.
















 Posted in:
Posted in:
0 comments:
Post a Comment